Our relationship to privacy has changed radically since the widespread adoption of the internet. While it once was difficult to broadcast our message to an audience, it’s now a challenge to limit the reach of our communications and control our personal data. This course responds to our always public condition in a graphic design context – tracing the connection between encryption and Graphic Design back to Graphic Design's origins with printing, and by challenging students to question and create methods for private communication today.
Students will research the entities monitoring our information and communications. Then, through form-making, production, and distribution, students will produce their own cryptographic methods to anonymize their communications, circumvent surveillance, and take control of their information and communication channels. Questioning power structures, embracing anonymity, and finding and celebrating the beauty in the process of hiding and revealing.
This course’s efforts will be divided in two parts:
1. Decryption
The first will focus on 'decrypting' the people, parties, entities, and technologies that surveil and transmit our communications. By unlocking their methods of surveilance through form-making and displaying them, we’ll elucidate their machinations, generate poetic works, and make clear otherwise opaque systems.
Even our seemingly private information is open to monitoring. Technically, our digital communications need to be recorded and processed in order to be transferred. Commercially, it’s in the interest of technology companies to analyze our information in order to deliver the ‘best’ ‘user experience’. Adversely, outside actors have an interest in gaining access to our data, from governments to hackers to unwanted attention from friends and family, for myriad reasons.
Over the past century design and art has responded to these developments both formally and conceptually. Grappling with notions of transparency, modernization, and technology as physical media dematerialized, and communication became more fluid.
The first part of the class will be dedicated to research through making (and traditional research). We'll execute a series of short 'studies' that address specific aspects of privacy and design today, and compile them into a group publication we publish at the mid-term.
Study 1A: Self-Portrait
What is your digital image? How do our online actions create an impression of us and who defines it? Students will explore the myriad audiences embedded in our day-to-day communications, and designer's roles in mediating them, from the government agencies monitoring our online messages to our peer groups, and how they characterize us.
We'll research this topic then create a graphic self-portrait that juxtaposes our online identity(ies) with the processes used to create them.
 Autobiography – Sol Lewitt
Autobiography – Sol Lewitt
 Cache Self-Portrait – Evan Roth
Cache Self-Portrait – Evan Roth
 High School Uni-Face: Girl – Do Ho Suh
High School Uni-Face: Girl – Do Ho Suh
 High School Uni-Face: Boy – Do Ho Suh
High School Uni-Face: Boy – Do Ho Suh
Study 1B: Movement
Dating back to the invention of cinematography, which was used to analyze, then optimize, and regulate factory workers’ bodily movements1, human physicality has been a valuable commodity. Today, the monitoring of our person – our vital signs and location – have become increasingly detailed and scrutinized.
We'll analyze the ways our movements are monitored from a macro to a micro level. Students will then create a map based on these findings that visualizes, and questions, the different ways our movements are being tracked.
 Merciless Separation – Constant Dullaart
Merciless Separation – Constant Dullaart
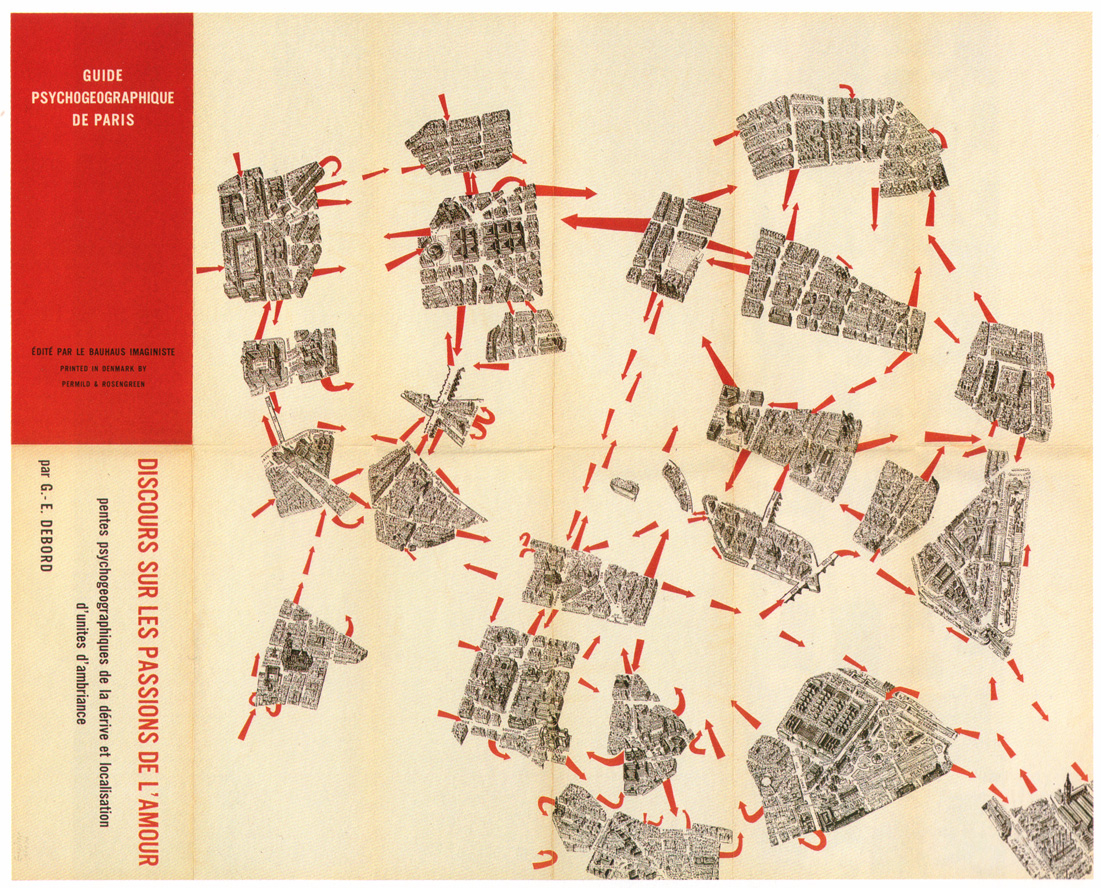 PsychoGeography – Guy Debord
PsychoGeography – Guy Debord
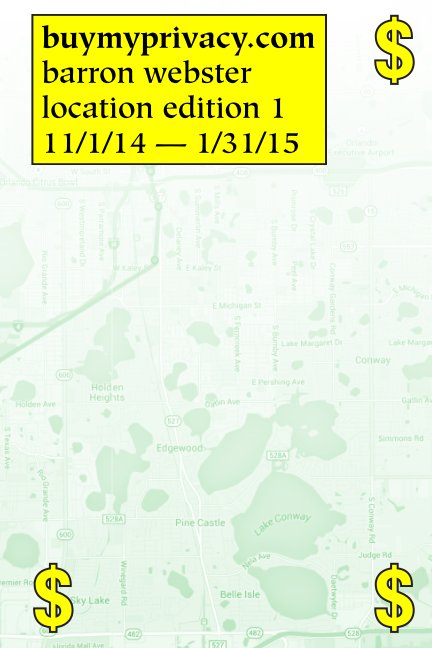 Buy My Privacy: Location Edition – Barron Webster
Buy My Privacy: Location Edition – Barron Webster
Study 1C: Machine Vision
Machine intelligence is becoming more common in our communications systems – mediating, analyzing, and responding to our actions. This enables once unimaginable forms of communications, analysis, and experiences. However, their processes are often opaque – following logics that are often hard to grasp and can be in conflict to the modernist ideals that inform much of today's product design.
We'll test the thresholds of these systems visual capabilities in a pattern-making exercise.
 Blank Process – Clement Valla
Blank Process – Clement Valla
 Gender Shades – Joy Buolamwini
Gender Shades – Joy Buolamwini
 Shirley Cards
Shirley Cards
2. Encryption
In the second part of the course we’ll focus on developing our own cryptographic methods for private communications. These methods will respond to, and incorporate, the research around surveillance we conducted in the first part of the course.
We'll look at historic and current methods of encryption – ranging from traditional ciphers to those enabled by emmerging technologies. And work to understand Graphic Design's role in encryption, and how the practice can be used in non-traditional ways.
By now we'll have identified the parties: tech companies, government agencies. The methods: biometric analysis, algorithms, multi-sensory recorders, our phones, computers, and smart devices. And the motivations: competitive marketplace advantage, and national security. As well as many other unforseen aspects that lead to surveillance and interference. We'll question our role in these systems as designers and individuals, and evaluate our stances on these issues.
After a quick introductory study, students will create an encryption method based on their personal interest. At the end of the semester we'll embed our works within CCA as an 'exhibition'.
Open Project / Embedded Exhibition
In this open-ended project you'll create your own method to encrypt communications. This can take many forms: a process to evade algorithms, a typeface that only specific audiences can read, a technical solution that scrambles your IP address.
There will be two outcomes for the project – your method and an artifact made with it that we'll embed on campus in an 'exhibition'. The exhibition will be a collective effort to which we'll all contribute, striving to engage with the topics we've researched and methodologies we've developed.
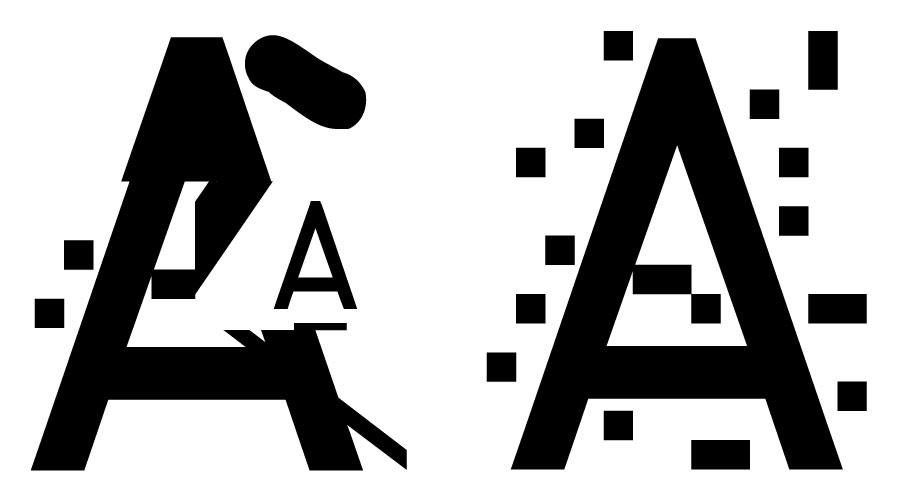 ZXX – Sang Mun
ZXX – Sang Mun
 Technical Drawings – Sulki and Min
Technical Drawings – Sulki and Min
 Jennifer in Paradise – Constant Dullaart
Jennifer in Paradise – Constant Dullaart